 Phishing is one of the most insidious data security threats to an individual and a business, taking advantage of your weakest security link: people. Phishing is the attempt to obtain personal and business security information by pretending to be a legitimate email communication from a trusted source.
Phishing is one of the most insidious data security threats to an individual and a business, taking advantage of your weakest security link: people. Phishing is the attempt to obtain personal and business security information by pretending to be a legitimate email communication from a trusted source.
Here’s a recent example of just such a communication that came in to our lead network engineer, Henry:
From: Apple Global Service Exchange <gsx_reply@apple.com>
Date: March 16, 2015 at 6:15:16 PM EDT
To: Undisclosed recipients:;
Subject: Your GSX account need update.
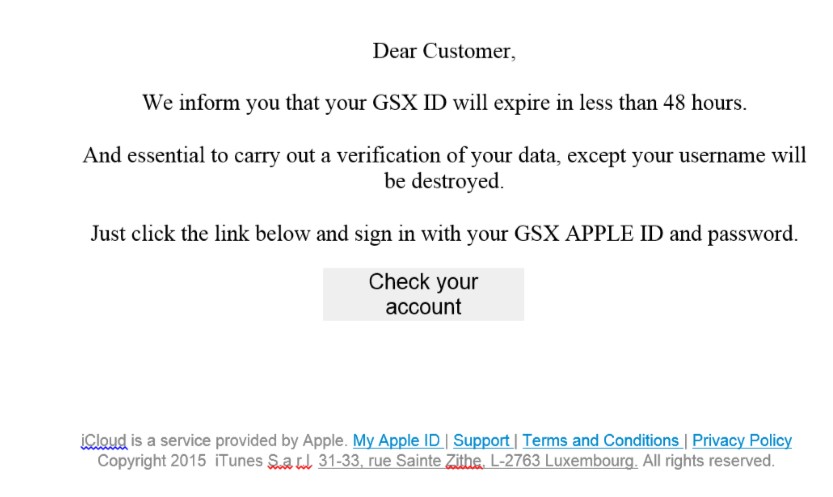
On the surface, the email looks legitimate and might immediately cause alarm to the recipient. But were you to click on “check your account,” the link would not take you to Apple; instead, it would take you to laflores.net, a website that looks like an exact replica of the Apple sign-in page. Had Henry fallen for the email and entered his information, laflores.net would have his Apple ID, access to whatever account information he had stored there, and possibly enough information to do real harm.
This is an example of a classic phishing attempt. From fake GSX requests to warnings from your bank that your account has been compromised, thereby encouraging you to log in and change your password, every individual who is duped into responding to one of these messages is putting personal and company information at harm.
How Can Your Business Protect Itself from Phishing?
The most important step you can take to protect yourself from phishing, or any cyber-attack, is to have the best network security and enterprise threat detection available. But as you can see from the email that Henry received, phishing emails are still going to reach your employees, so the other effort business leaders must make to protect themselves is to train employees to recognize and reject these emails.
Anti-Phishing Guide
Cybercriminals are insidious and will prey on fear. While emails are most common, pop-up messages warning you that something is wrong will also be used to create enough fear to get someone to click on the links. Some cybercriminals will even phone you to perpetrate the scam.
Teach your employees to watch for these indications of email phishing:
- The email may not address you personally or refer to your specific user name.
- The link will look legitimate on the surface but the url will go somewhere other than the company marketed. Hover over the link (without clicking) to see the actual URL. The link may even be very similar to the actual company URL, so be cautious. Rather than click the link, open a new browser and manually type in the actual link of the website in question if you need to check your account status.
- Many phishing emails will contain syntax or grammar errors. They may have spelling mistakes. If you look closely at the sample above, you’ll see the grammar is off and there are punctuation errors. A professional organization would not send something like this.
- The email may have a threatening overtone, making it seem that urgent action is required to protect your account.
- Cybercriminals may even call, pretending to represent the company in question, then ask you for personal information in order to access your account. Most legitimate companies will not make outgoing calls to solicit this information. Hang up and call back to the company’s legitimate support number to verify.
Humans are easy targets because our emotions can be manipulated. A level of skepticism is required in order to keep your personal and business security intact. When in doubt:
- Don’t click a link
- Don’t open a file
- Don’t provide personal information
- Don’t download anything from unknown sources
Feel free to use this guide with your employees. If you are concerned about your business network security, contact thinkCSC to learn more.
 On May 14 and 15 at Kalahari Resort in Sandusky, the Instructional Technology Integration Partnership of Ohio (ITIP Ohio) is hosting an edtech summit featuring Google for Education. With sessions such as “Google Classroom 101” and “Preparing Chrome Books for Online Testing,” school administrators will have the opportunity to learn how to make the most of the technology that is becoming commonplace in every school.
On May 14 and 15 at Kalahari Resort in Sandusky, the Instructional Technology Integration Partnership of Ohio (ITIP Ohio) is hosting an edtech summit featuring Google for Education. With sessions such as “Google Classroom 101” and “Preparing Chrome Books for Online Testing,” school administrators will have the opportunity to learn how to make the most of the technology that is becoming commonplace in every school.



Recent Comments